What is sandboxing?
Apple introduced App Sandbox in Mac OS X Leopard (10.5) to allow developers to “sandbox” their applications. Sandboxing refers to restrictions on what system resources an application can access: files, folders, operating system features, and hardware components such as the camera or microphone.
The main purpose of sandboxing is to protect your Mac in case the application is damaged or compromised by a malicious attack: a sandboxed app can’t steal or destroy personal data if it hasn’t been granted access to them.
For an in-depth technical explanation of sandboxing in macOS, go to About App Sandbox on the Apple Developer site.
Sandboxed vs. non-sandboxed applications
Apple requires that applications sold in the Mac App Store must use App Sandbox as of June 1, 2012. Some third-party developers sell their applications both through the Mac App Store and through direct sales. Versions sold through direct sale and through the Mac App Store may both use App Sandbox, but in many cases the direct-sale version has functionality that Mac App Store restrictions doesn’t allow.
How can I tell which applications are sandboxed?
You can see which applications use App Sandbox in Activity Monitor by adding a column to the table of processes.
- Open Activity Monitor (/Applications/Utilities/Activity Monitor)
- Control-click on a column header; a dropdown menu appears
- Select Sandbox; a Sandbox column will be added to the table
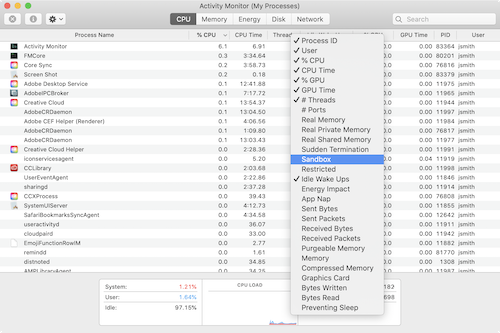
Applications which use the built-in macOS sandboxing features will have a “Yes” in that column.
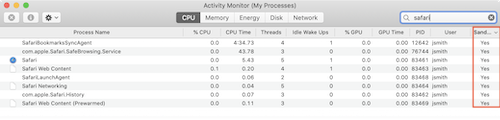
Some developers implement their own sandboxing model instead of using App Sandbox, so Activity Monitor may not list them as sandboxed.
How does sandboxing affect font activation?
Applications which use App Sandbox are unable to use fonts that aren’t located in one of the operating system font folders:
- /System/Library/Fonts/
- /Library/Fonts/
- /Users/username/Library/Fonts/
Universal Type Client stores fonts in /Library/Extensis/UTC/ instead of in an operating system font folder. Sandboxed applications that try to use fonts in Universal Type Client will be blocked by App Sandbox; the effects can vary based on the application. Some applications may prompt you to enter your macOS username and password to grant access to the font. Other applications will replace the requested font with a placeholder font such as .LastResort, Calibri, or Myriad. If you have questions about how a specific application uses sandboxing, you should check with the developer.
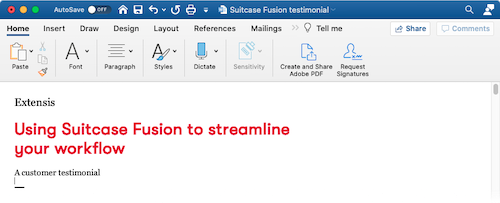
A sample of text in Microsoft Word 365
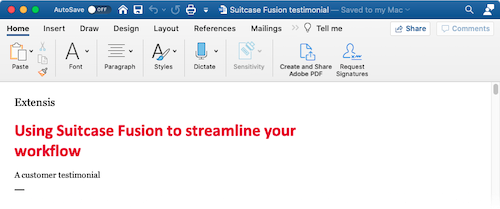
The same text with a placeholder font
Resolving font conflicts in sandboxed applications
Apple has yet to provide a method for making fonts or other resources available to sandboxed applications. Until they do, the easiest way to prevent problems is to avoid using fonts that are not in an operating system font folder when working in applications such as Keynote, Microsoft Word, Pages, or Safari. If you have fonts that must be used in those applications, you should keep copies of those fonts in the /Library/Fonts/ or /Users/username/Library/Fonts/ folder.
Note: Universal Type Client can activate duplicates of fonts that reside in an operating system font folder, overriding the system font. Deactivate the copies in Universal Type Client to allow macOS to use the system-supplied version.